Row brews as academics uncover flaws in bank card Chip and PIN technology
Member: Nifa
The publication of the postgraduate paper highlighting the discovery by scientists at Cambridge University of flaws in the chip and PIN technology used to secure credit and debit card transactions has led to a major row between academics and the banking industry.
The UK Cards Association (UKCA), which represents the country’s biggest banks, wrote to the university to try to remove the online publication of research which shows how a hand-held device, costing twenty pounds, could be used to buy goods without entering the correct PIN.
Melanie Johnson, Chief Executive of the UKCA, said that the publication "overstepped the boundaries of what constitutes responsible disclosure", adding that the type of attack described was "difficult to undertake" and "unlikely to interest genuine fraudsters".
She went on to say that the "level of detail" published was worrying and asked for the research to be removed. Police, she added, had expressed concern the student "was allowed to falsify a transaction in a shop in Cambridge without first warning the merchant".
But, Ross Anderson, professor of security engineering at Cambridge University’s Computer Laboratory, said: "This was absolutely unacceptable. It was a very very nasty attempt at censorship."
He said exposing vulnerabilities in the system was an example of "responsible disclosure" and said the industry had been guilty of "sitting on their butts and doing nothing" since he and fellow scientists first revealed the flaw in late 2009.
In a written response to the UKCA, Professor Anderson wrote: "You seem to think that we might censor a student’s thesis, which is lawful and already in the public domain, simply because a powerful interest finds it inconvenient."
"This shows a deep misconception of what universities are and how we work. Cambridge is the University of Erasmus, of Newton, and of Darwin; censoring writings that offend the powerful is offensive to our deepest values."
He continued: "You complain that our work may undermine public confidence in the payments system. What will support public confidence in the payments system is evidence that the banks are frank and honest in admitting its weaknesses when they are exposed, and diligent in effecting the necessary remedies. Your letter shows that, instead, your member banks do their lamentable best to deprecate the work of those outside their cosy club, and indeed to censor it."
Prof Anderson said he had authorised the thesis to be issued as a Computer Laboratory technical report, saying: "This will make it easier for people to find and to cite, and will ensure that its presence on our website is permanent."
He said there was no basis for police concern as there was no intent to commit fraud, as the card holder gave his consent and the merchant was paid.
He added that Barclays Bank did appear to have closed the technological loophole although other banks were yet to fix the problem.
A UKCA spokeswoman said: "The UK Cards Association had written to Cambridge not to challenge the work of the university’s security academics but only to challenge whether publishing explicit details of how to attempt a fraud – specifically one which there is no evidence of a fraudster yet undertaking – is necessary and serving the public’s best interest.
"We remain hopeful that the academics concerned will work with us rather than against us to help defeat the fraudsters – as unfortunately it is only the fraudsters who stand to gain from any lack of cooperation between us."
She said it was questionable whether publishing what the UKCA called a "DIY guide for fraudsters’ was "in the best interests of the card-holding public".
And she added while "nothing is 100% secure" fraud on UK issued cards had dropped to 186.8 million pounds in the first six months of the year, down 20% on the same period in 2009.
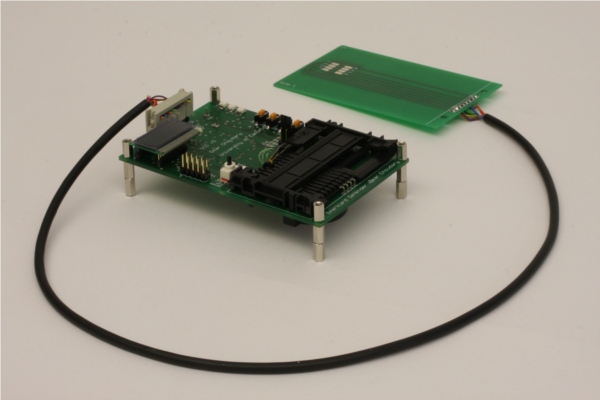
Photograph of device reproduced courtesy of University of Cambridge
ENDS
Share on Twitter
